先日、Oracle CloudでCentOS8のインスタンスを作成し、Streamに変換しました。
あれから少し経ってCentOS8のインスタンスを再度、新規で作成し、バージョンを確認するとRed Hat Enterprise Linux release 8.3となっておりこの前とは違っていました。
VMを作成したばかりの状態がどうなっているかを確認しつつ、CentOSと互換性がある、このLinuxにデフォルトでインストール済みのファイアーウォールでポート開放などを試します。
実践がメインとしたいので、詳しい説明はしませんが、下記のページでコンセプトを確認できます。
https://firewalld.org/documentation/concepts.html
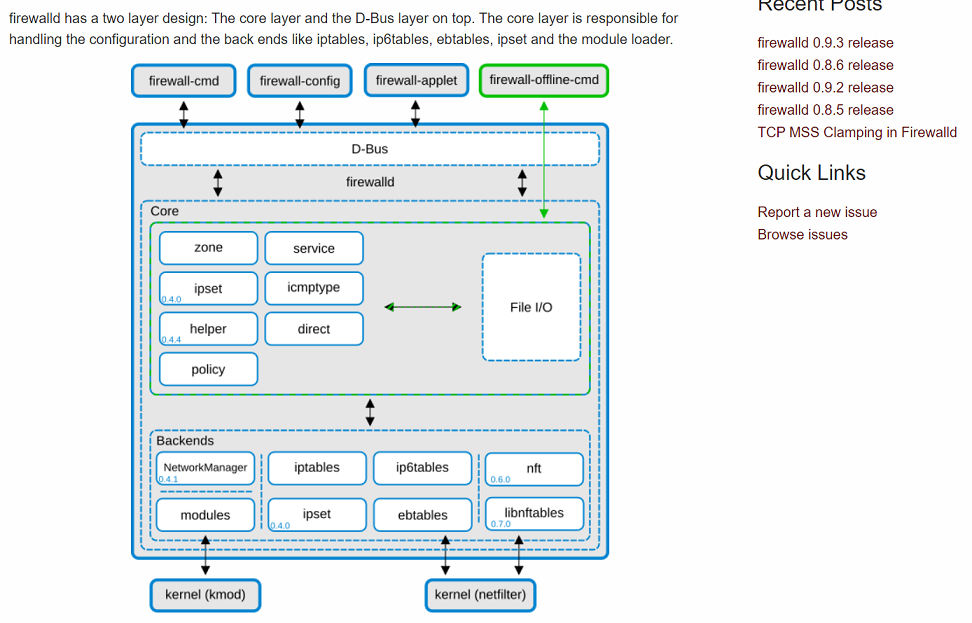
Red Hat Enterprise Linux release 8ではiptablesがnftablesに変更になり、firewalldのバックエンドになったみたいです。firewalldが稼働していることが確認できます。
sudo systemctl status firewalldnftablesは無効になっていますが、nftablesが含んでいるコマンドで確認することはできることだけ覚えておこうと思います。
sudo nft list ruleset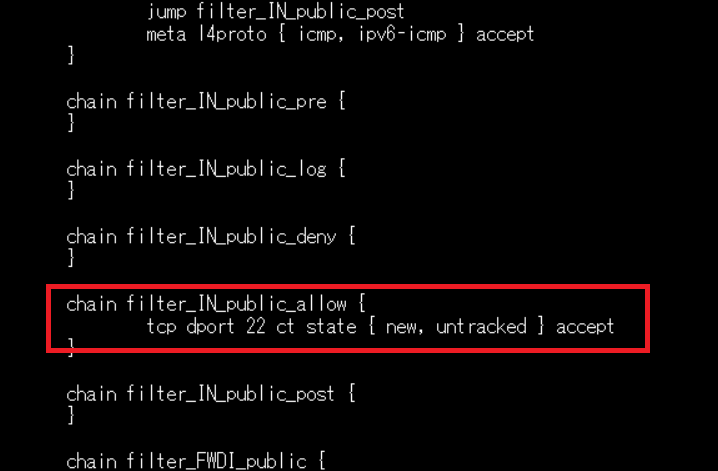
table ip filter {
chain INPUT {
type filter hook input priority filter; policy accept;
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
@nh,128,16 43518 counter packets 34708 bytes 2682940 jump BareMetalInstanceServices
}
chain BareMetalInstanceServices {
meta l4proto tcp ip daddr 169.254.0.2 skuid 0 tcp dport 3260 counter packets 0 bytes 0 accept
meta l4proto tcp @nh,128,24 11140610 skuid 0 tcp dport 3260 counter packets 0 bytes 0 accept
meta l4proto tcp @nh,128,24 11140612 skuid 0 tcp dport 3260 counter packets 0 bytes 0 accept
meta l4proto tcp @nh,128,24 11140613 skuid 0 tcp dport 3260 counter packets 0 bytes 0 accept
meta l4proto tcp ip daddr 169.254.0.2 tcp dport 80 counter packets 0 bytes 0 accept
meta l4proto udp ip daddr 169.254.169.254 udp dport 53 counter packets 7853 bytes 710133 accept
meta l4proto tcp ip daddr 169.254.169.254 tcp dport 53 counter packets 0 bytes 0 accept
meta l4proto tcp ip daddr 169.254.0.3 skuid 0 tcp dport 80 counter packets 0 bytes 0 accept
meta l4proto tcp ip daddr 169.254.0.4 tcp dport 80 counter packets 0 bytes 0 accept
meta l4proto tcp ip daddr 169.254.169.254 tcp dport 80 counter packets 26637 bytes 1954231 accept
meta l4proto udp ip daddr 169.254.169.254 udp dport 67 counter packets 4 bytes 1312 accept
meta l4proto udp ip daddr 169.254.169.254 udp dport 69 counter packets 0 bytes 0 accept
meta l4proto udp ip daddr 169.254.169.254 udp dport 123 counter packets 212 bytes 16112 accept
meta l4proto tcp @nh,128,16 43518 counter packets 0 bytes 0 reject with tcp reset
meta l4proto udp @nh,128,16 43518 counter packets 0 bytes 0 reject
}
}
table ip6 filter {
chain INPUT {
type filter hook input priority filter; policy accept;
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
}
}
table bridge filter {
chain INPUT {
type filter hook input priority filter; policy accept;
}
chain FORWARD {
type filter hook forward priority filter; policy accept;
}
chain OUTPUT {
type filter hook output priority filter; policy accept;
}
}
table ip security {
chain INPUT {
type filter hook input priority 150; policy accept;
}
chain FORWARD {
type filter hook forward priority 150; policy accept;
}
chain OUTPUT {
type filter hook output priority 150; policy accept;
}
}
table ip raw {
chain PREROUTING {
type filter hook prerouting priority raw; policy accept;
}
chain OUTPUT {
type filter hook output priority raw; policy accept;
}
}
table ip mangle {
chain PREROUTING {
type filter hook prerouting priority mangle; policy accept;
}
chain INPUT {
type filter hook input priority mangle; policy accept;
}
chain FORWARD {
type filter hook forward priority mangle; policy accept;
}
chain OUTPUT {
type route hook output priority mangle; policy accept;
}
chain POSTROUTING {
type filter hook postrouting priority mangle; policy accept;
}
}
table ip nat {
chain PREROUTING {
type nat hook prerouting priority dstnat; policy accept;
}
chain INPUT {
type nat hook input priority 100; policy accept;
}
chain POSTROUTING {
type nat hook postrouting priority srcnat; policy accept;
}
chain OUTPUT {
type nat hook output priority -100; policy accept;
}
}
table ip6 security {
chain INPUT {
type filter hook input priority 150; policy accept;
}
chain FORWARD {
type filter hook forward priority 150; policy accept;
}
chain OUTPUT {
type filter hook output priority 150; policy accept;
}
}
table ip6 raw {
chain PREROUTING {
type filter hook prerouting priority raw; policy accept;
}
chain OUTPUT {
type filter hook output priority raw; policy accept;
}
}
table ip6 mangle {
chain PREROUTING {
type filter hook prerouting priority mangle; policy accept;
}
chain INPUT {
type filter hook input priority mangle; policy accept;
}
chain FORWARD {
type filter hook forward priority mangle; policy accept;
}
chain OUTPUT {
type route hook output priority mangle; policy accept;
}
chain POSTROUTING {
type filter hook postrouting priority mangle; policy accept;
}
}
table ip6 nat {
chain PREROUTING {
type nat hook prerouting priority dstnat; policy accept;
}
chain INPUT {
type nat hook input priority 100; policy accept;
}
chain POSTROUTING {
type nat hook postrouting priority srcnat; policy accept;
}
chain OUTPUT {
type nat hook output priority -100; policy accept;
}
}
table bridge nat {
chain PREROUTING {
type filter hook prerouting priority dstnat; policy accept;
}
chain OUTPUT {
type filter hook output priority out; policy accept;
}
chain POSTROUTING {
type filter hook postrouting priority srcnat; policy accept;
}
}
table inet firewalld {
chain raw_PREROUTING {
type filter hook prerouting priority raw + 10; policy accept;
icmpv6 type { nd-router-advert, nd-neighbor-solicit } accept
meta nfproto ipv6 fib saddr . iif oif missing drop
jump raw_PREROUTING_ZONES_SOURCE
jump raw_PREROUTING_ZONES
}
chain raw_PREROUTING_ZONES_SOURCE {
}
chain raw_PREROUTING_ZONES {
iifname "ens3" goto raw_PRE_public
goto raw_PRE_public
}
chain mangle_PREROUTING {
type filter hook prerouting priority mangle + 10; policy accept;
jump mangle_PREROUTING_ZONES_SOURCE
jump mangle_PREROUTING_ZONES
}
chain mangle_PREROUTING_ZONES_SOURCE {
}
chain mangle_PREROUTING_ZONES {
iifname "ens3" goto mangle_PRE_public
goto mangle_PRE_public
}
chain filter_INPUT {
type filter hook input priority filter + 10; policy accept;
ct state { established, related } accept
ct status dnat accept
iifname "lo" accept
jump filter_INPUT_ZONES_SOURCE
jump filter_INPUT_ZONES
ct state { invalid } drop
reject with icmpx type admin-prohibited
}
chain filter_FORWARD {
type filter hook forward priority filter + 10; policy accept;
ct state { established, related } accept
ct status dnat accept
iifname "lo" accept
ip6 daddr { ::/96, ::ffff:0.0.0.0/96, 2002::/24, 2002:a00::/24, 2002:7f00::/24, 2002:a9fe::/32, 2002:ac10::/28, 2002:c0a8::/32, 2002:e000::/19 } reject with icmpv6 type addr-unreachable
jump filter_FORWARD_IN_ZONES_SOURCE
jump filter_FORWARD_IN_ZONES
jump filter_FORWARD_OUT_ZONES_SOURCE
jump filter_FORWARD_OUT_ZONES
ct state { invalid } drop
reject with icmpx type admin-prohibited
}
chain filter_OUTPUT {
type filter hook output priority filter + 10; policy accept;
oifname "lo" accept
ip6 daddr { ::/96, ::ffff:0.0.0.0/96, 2002::/24, 2002:a00::/24, 2002:7f00::/24, 2002:a9fe::/32, 2002:ac10::/28, 2002:c0a8::/32, 2002:e000::/19 } reject with icmpv6 type addr-unreachable
}
chain filter_INPUT_ZONES_SOURCE {
}
chain filter_INPUT_ZONES {
iifname "ens3" goto filter_IN_public
goto filter_IN_public
}
chain filter_FORWARD_IN_ZONES_SOURCE {
}
chain filter_FORWARD_IN_ZONES {
iifname "ens3" goto filter_FWDI_public
goto filter_FWDI_public
}
chain filter_FORWARD_OUT_ZONES_SOURCE {
}
chain filter_FORWARD_OUT_ZONES {
oifname "ens3" goto filter_FWDO_public
goto filter_FWDO_public
}
chain raw_PRE_public {
jump raw_PRE_public_pre
jump raw_PRE_public_log
jump raw_PRE_public_deny
jump raw_PRE_public_allow
jump raw_PRE_public_post
}
chain raw_PRE_public_pre {
}
chain raw_PRE_public_log {
}
chain raw_PRE_public_deny {
}
chain raw_PRE_public_allow {
}
chain raw_PRE_public_post {
}
chain filter_IN_public {
jump filter_IN_public_pre
jump filter_IN_public_log
jump filter_IN_public_deny
jump filter_IN_public_allow
jump filter_IN_public_post
meta l4proto { icmp, ipv6-icmp } accept
}
chain filter_IN_public_pre {
}
chain filter_IN_public_log {
}
chain filter_IN_public_deny {
}
chain filter_IN_public_allow {
tcp dport 22 ct state { new, untracked } accept
}
chain filter_IN_public_post {
}
chain filter_FWDI_public {
jump filter_FWDI_public_pre
jump filter_FWDI_public_log
jump filter_FWDI_public_deny
jump filter_FWDI_public_allow
jump filter_FWDI_public_post
meta l4proto { icmp, ipv6-icmp } accept
}
chain filter_FWDI_public_pre {
}
chain filter_FWDI_public_log {
}
chain filter_FWDI_public_deny {
}
chain filter_FWDI_public_allow {
}
chain filter_FWDI_public_post {
}
chain mangle_PRE_public {
jump mangle_PRE_public_pre
jump mangle_PRE_public_log
jump mangle_PRE_public_deny
jump mangle_PRE_public_allow
jump mangle_PRE_public_post
}
chain mangle_PRE_public_pre {
}
chain mangle_PRE_public_log {
}
chain mangle_PRE_public_deny {
}
chain mangle_PRE_public_allow {
}
chain mangle_PRE_public_post {
}
chain filter_FWDO_public {
jump filter_FWDO_public_pre
jump filter_FWDO_public_log
jump filter_FWDO_public_deny
jump filter_FWDO_public_allow
jump filter_FWDO_public_post
}
chain filter_FWDO_public_pre {
}
chain filter_FWDO_public_log {
}
chain filter_FWDO_public_deny {
}
chain filter_FWDO_public_allow {
}
chain filter_FWDO_public_post {
}
}
table ip firewalld {
chain nat_PREROUTING {
type nat hook prerouting priority dstnat + 10; policy accept;
jump nat_PREROUTING_ZONES_SOURCE
jump nat_PREROUTING_ZONES
}
chain nat_PREROUTING_ZONES_SOURCE {
}
chain nat_PREROUTING_ZONES {
iifname "ens3" goto nat_PRE_public
goto nat_PRE_public
}
chain nat_POSTROUTING {
type nat hook postrouting priority srcnat + 10; policy accept;
jump nat_POSTROUTING_ZONES_SOURCE
jump nat_POSTROUTING_ZONES
}
chain nat_POSTROUTING_ZONES_SOURCE {
}
chain nat_POSTROUTING_ZONES {
oifname "ens3" goto nat_POST_public
goto nat_POST_public
}
chain nat_PRE_public {
jump nat_PRE_public_pre
jump nat_PRE_public_log
jump nat_PRE_public_deny
jump nat_PRE_public_allow
jump nat_PRE_public_post
}
chain nat_PRE_public_pre {
}
chain nat_PRE_public_log {
}
chain nat_PRE_public_deny {
}
chain nat_PRE_public_allow {
}
chain nat_PRE_public_post {
}
chain nat_POST_public {
jump nat_POST_public_pre
jump nat_POST_public_log
jump nat_POST_public_deny
jump nat_POST_public_allow
jump nat_POST_public_post
}
chain nat_POST_public_pre {
}
chain nat_POST_public_log {
}
chain nat_POST_public_deny {
}
chain nat_POST_public_allow {
}
chain nat_POST_public_post {
}
}
table ip6 firewalld {
chain nat_PREROUTING {
type nat hook prerouting priority dstnat + 10; policy accept;
jump nat_PREROUTING_ZONES_SOURCE
jump nat_PREROUTING_ZONES
}
chain nat_PREROUTING_ZONES_SOURCE {
}
chain nat_PREROUTING_ZONES {
iifname "ens3" goto nat_PRE_public
goto nat_PRE_public
}
chain nat_POSTROUTING {
type nat hook postrouting priority srcnat + 10; policy accept;
jump nat_POSTROUTING_ZONES_SOURCE
jump nat_POSTROUTING_ZONES
}
chain nat_POSTROUTING_ZONES_SOURCE {
}
chain nat_POSTROUTING_ZONES {
oifname "ens3" goto nat_POST_public
goto nat_POST_public
}
chain nat_PRE_public {
jump nat_PRE_public_pre
jump nat_PRE_public_log
jump nat_PRE_public_deny
jump nat_PRE_public_allow
jump nat_PRE_public_post
}
chain nat_PRE_public_pre {
}
chain nat_PRE_public_log {
}
chain nat_PRE_public_deny {
}
chain nat_PRE_public_allow {
}
chain nat_PRE_public_post {
}
chain nat_POST_public {
jump nat_POST_public_pre
jump nat_POST_public_log
jump nat_POST_public_deny
jump nat_POST_public_allow
jump nat_POST_public_post
}
chain nat_POST_public_pre {
}
chain nat_POST_public_log {
}
chain nat_POST_public_deny {
}
chain nat_POST_public_allow {
}
chain nat_POST_public_post {
}
}
chain filter_IN_public_allowの所にポート番号22が記述されております。ですのでSSH接続ができるわけですね。
実際に起動しているのはFirewalldなので、こちらでポート開放をしてみます。
最初に状態を確認して、ポート番号3306を開放してみます。データベースで使用するポートで外部からアクセス可能にします。
sudo firewall-cmd --zone=public --list-services
sudo firewall-cmd --zone=public --add-port=3306/tcp --permanent
sudo firewall-cmd --reload
sudo firewall-cmd --zone=public --list-port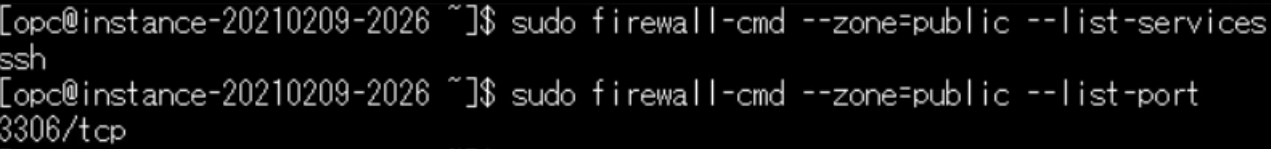
nftables関連のコマンド入力をすると、こちらでも確認ができました。
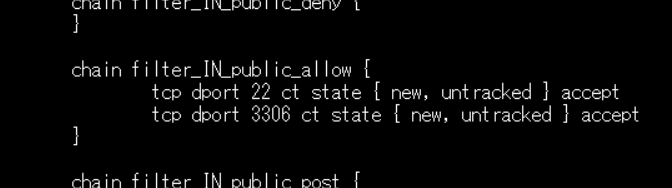
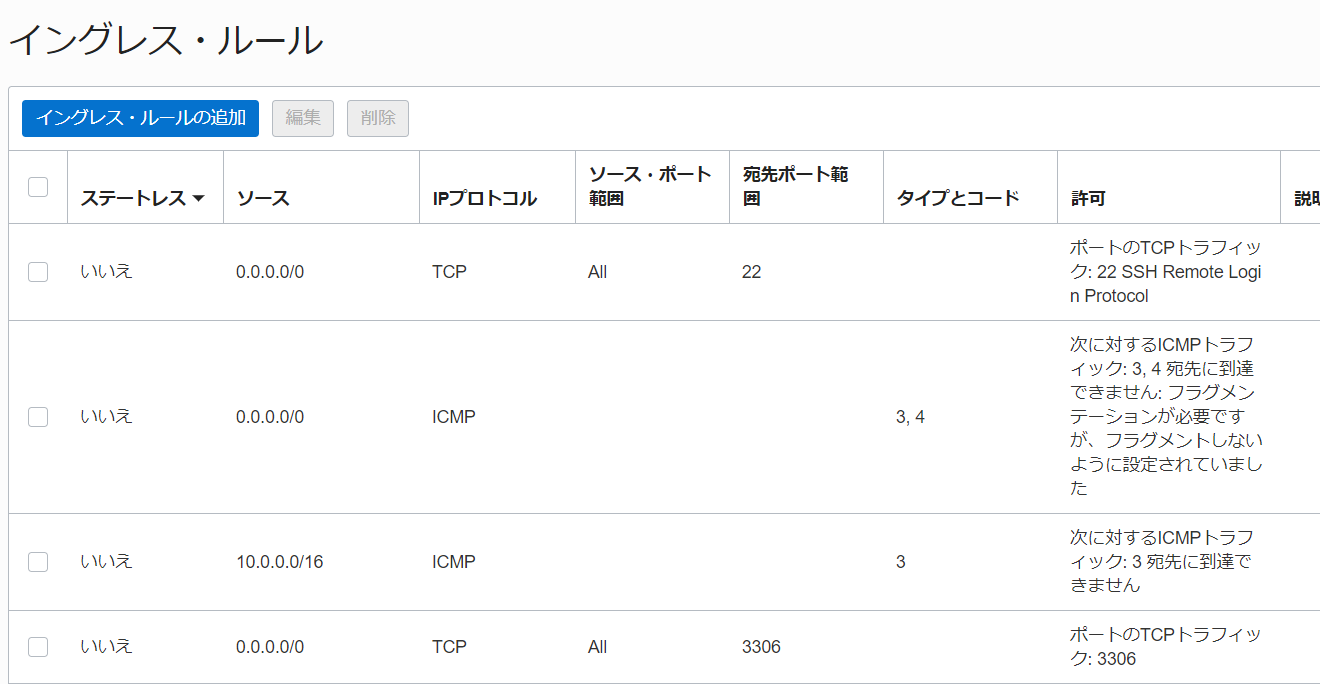
その後、忘れずにOracle Cloudのページでもこの番号を空けておきます。
コメント